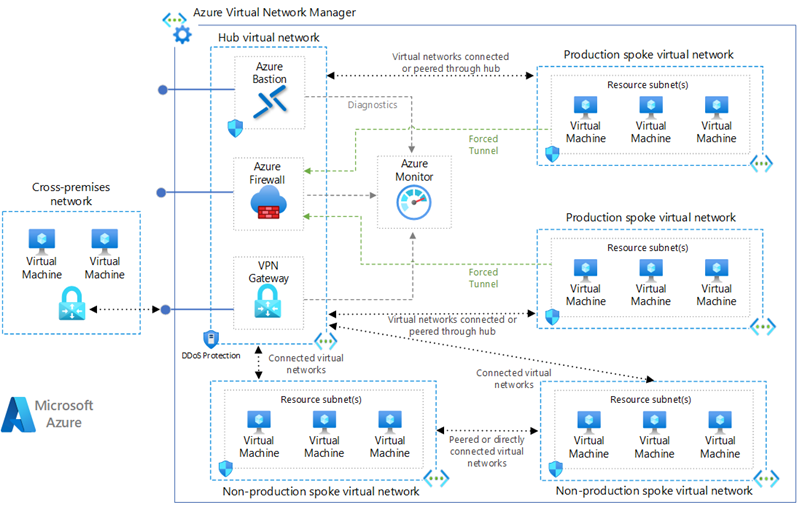
Hub-and-spoke topology in Azure is a network configuration that uses a central hub to connect multiple spokes. The hub is a virtual network (VNet) that acts as a central point of connectivity to many spoke VNets. The spokes are VNets that peer with the hub and can be used to isolate workloads while sharing services protected by the hub. This topology simplifies network management and reduces the potential for costly network traffic charges by keeping traffic within the Azure network.
Benefits of Hub-and-Spoke Topology
- Centralized Management: Centralized resources like network virtual appliances and gateways in the hub.
- Cost-effective: Reduces the need for redundant connections, thus minimizing costs.
- Security: Centralized security services like firewalls or intrusion detection systems.
- Isolation: Spokes can be used to isolate workloads, environments, or applications.
- Scalability: Easy to add new spokes as the organization grows.
Components of the Hub-and-Spoke Topology
- Hub Virtual Network: Contains shared services like Azure Firewall, VPN Gateway, and Azure Bastion.
- Spoke Virtual Networks: Contains resources such as virtual machines (VMs) and are connected to the hub via VNet peering.
- VPN Gateway: Connects on-premises networks to the Azure VNet.
- Azure Firewall: Provides a centralized, network-level protection.
- Azure Monitor: Monitors the health and connectivity of the network.
- DDoS Protection: Protects the Azure resources from DDoS attacks.