In today’s digitally connected world, organizations often need to manage and secure their devices efficiently. This includes the ability to remotely wipe devices in case they are lost or stolen. Microsoft 365 offers powerful tools for device management and security, and with PowerShell and Azure, you can automate the process of wiping devices when needed.
In this blog post, we will walk you through a PowerShell script that utilizes Azure and Microsoft Graph API to search for a user and remotely wipe their devices if necessary. We will also include some Azure screenshots to help you visualize the process.
Prerequisites
Before we begin, make sure you have the following prerequisites in place:
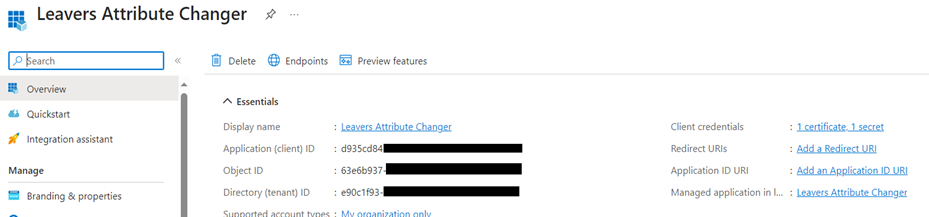
Azure AD App Registration: You will need to register an Azure AD App and obtain the AppID and AppSecret for authentication.
Microsoft 365 Tenant: You should have access to a Microsoft 365 tenant, and you’ll need to know the tenant ID (e.g., $Tenant = “YourTenantName”).
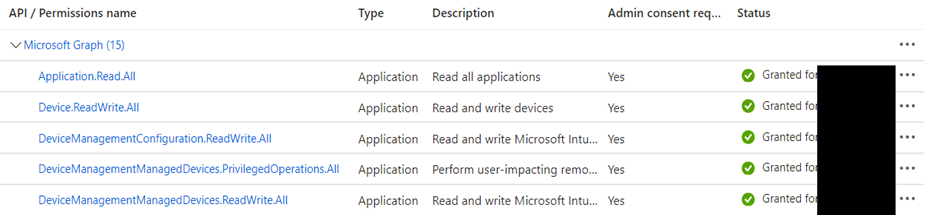
Microsoft Graph API: Make sure you have permissions to use the Microsoft Graph API and can authenticate with the provided App ID and App Secret.
The PowerShell Script
Let’s take a closer look at the PowerShell script that automates the device wipe process:
# Parameters for the script
Param (
$AppID = “YourAppID”,
$Scope = “https://graph.microsoft.com/.default”,
$Tenant = “YourTenantName”,
$AppSecret = “YourAppSecret”,
$GraphUrl = “https://login.microsoftonline.com/$($Tenant).onmicrosoft.com/oauth2/v2.0/token”,
$graph_endpoint = “https://graph.microsoft.com/v1.0″
)
# Get access token using client credentials grant flow
$Body = @{
client_id = $AppID
client_secret = $AppSecret
scope = $Scope
grant_type = ‘client_credentials’
}
$AuthorizationRequest = Invoke-RestMethod -Uri $GraphUrl -Method “Post” -Body $Body
$Access_token = $AuthorizationRequest.access_token
$Header = @{
Authorization = “Bearer ” + $AuthorizationRequest.access_token
“Content-Type” = “application/json”
}
# Connect to Microsoft Graph API
Connect-MgGraph -AccessToken $Access_token
# Specify the user’s email address
$user_email = “svc_test@yourdomain.com”
# Search for the user
$user_search_url = “$graph_endpoint/users?`$filter=userPrincipalName eq ‘$user_email'”
$user_response = Invoke-RestMethod -Header $header -Uri $user_search_url
if ($user_response.value.Count -eq 0) {
Write-Output “User not found!”
exit
}
$user_id = $user_response.value[0].id
# Find the user’s Intune devices
$devices_url = “$graph_endpoint/users/$user_id/ownedDevices”
$devices_response = Invoke-RestMethod -Headers $header -Uri $devices_url
if ($devices_response.value.Count -eq 0) {
Write-Output “No devices found for this user!”
exit
}
# Display devices and offer to wipe
foreach ($device in $devices_response.value) {
$device_id = $device.id
$device_name = $device.displayName
Write-Output “Device ID: $device_id – Name: $device_name”
$choice = Read-Host “Do you want to wipe this device? (yes/no)”
if ($choice -eq “yes”) {
$wipe_url = “$graph_endpoint/deviceManagement/managedDevices/$device_id/wipe”
$wipe_response = Invoke-RestMethod -Method Post -Headers $header -Uri $wipe_url
if ($wipe_response.StatusCode -eq 202) {
Write-Output “Device $device_name wipe initiated!”
} else {
Write-Output “Failed to wipe device $device_name. Status code: $($wipe_response.StatusCode)”
}
}
}
Write-Output “Script execution completed!”
The Script Explained
The script provided is focused on automating certain tasks in Microsoft Azure using the Azure Graph API. Let’s break down the key components of the script:
Parameters and Initialization
Param (
$AppID = “YourAppID”,
$Scope = “https://graph.microsoft.com/.default”,
$Tenant = “YourTenantName”,
$AppSecret = “YourAppSecret”,
$GraphUrl = “https://login.microsoftonline.com/$($Tenant).onmicrosoft.com/oauth2/v2.0/token”,
$graph_endpoint = “https://graph.microsoft.com/v1.0″
)
This section defines the parameters required for the script. These include the application ID, tenant details, application secret, Graph API URL.
Access Token Retrieval
$Body = @{
client_id = $AppID
client_secret = $AppSecret
scope = $Scope
grant_type = ‘client_credentials’
}
$AuthorizationRequest = Invoke-RestMethod -Uri $GraphUrl -Method “Post” -Body $Body
$Access_token = $AuthorizationRequest.access_token
This part of the script retrieves an access token from Azure, which is necessary for authenticating API requests.
User and Device Management
$user_email = svc_test@yourdomain.com
This section searches for a specific user and their associated Intune devices. It’s a practical approach for managing user accounts and their devices in a large organization.
You can also use the user as a parameter in case you want to create Azure Automation Account and or Logic App.
Device Wipe Feature
foreach ($device in $devices_response.value) {
$device_id = $device.id
$device_name = $device.displayName
Write-Output “Device ID: $device_id – Name: $device_name”
$choice = Read-Host “Do you want to wipe this device? (yes/no)”
if ($choice -eq “yes”) {
$wipe_url = “$graph_endpoint/deviceManagement/managedDevices/$device_id/wipe”
$wipe_response = Invoke-RestMethod -Method Post -Headers $header -Uri $wipe_url
if ($wipe_response.StatusCode -eq 202) {
Write-Output “Device $device_name wipe initiated!”
} else {
Write-Output “Failed to wipe device $device_name. Status code: $($wipe_response.StatusCode)”
}
}
}
Write-Output “Script execution completed!”
The script offers an option to wipe a device, an essential feature for managing company devices, especially in scenarios like employee offboarding.
Conclusion
This PowerShell script is a powerful tool for automating complex Azure operations. By leveraging the Azure Graph API, IT professionals can manage user accounts and devices efficiently, making their workflow smoother and more reliable. Remember to replace the placeholders with your specific Azure environment details to ensure the script works correctly in your setting. Automation in Azure not only saves time but also enhances the overall security and management of IT resources.